Operating entirely in the cloud, SaaS solutions are vulnerable to various threats. For this reason, security should be the top priority when you decide to build a SaaS product. Fortunately, the industry in today’s state offers a myriad of ways to create, improve, and optimize the security of your solution.
In this article, we will overview why it is so important, mention common challenges as well as list some of the best practices to protect the solution.
Why is SaaS security important?
Since all of the data needed for it to operate is stored on cloud servers, SaaS security standards are the primary concern. The goal for vendors is to ensure quality services and provide all the SaaS advantages to their users. To this end, vendors should guarantee the maintenance and security of all the layers that form SaaS architecture - infrastructure, network, and software.
Companies that fail to protect their software can pay a high price when targeted by cybercrimes. Here are several facts for you to consider
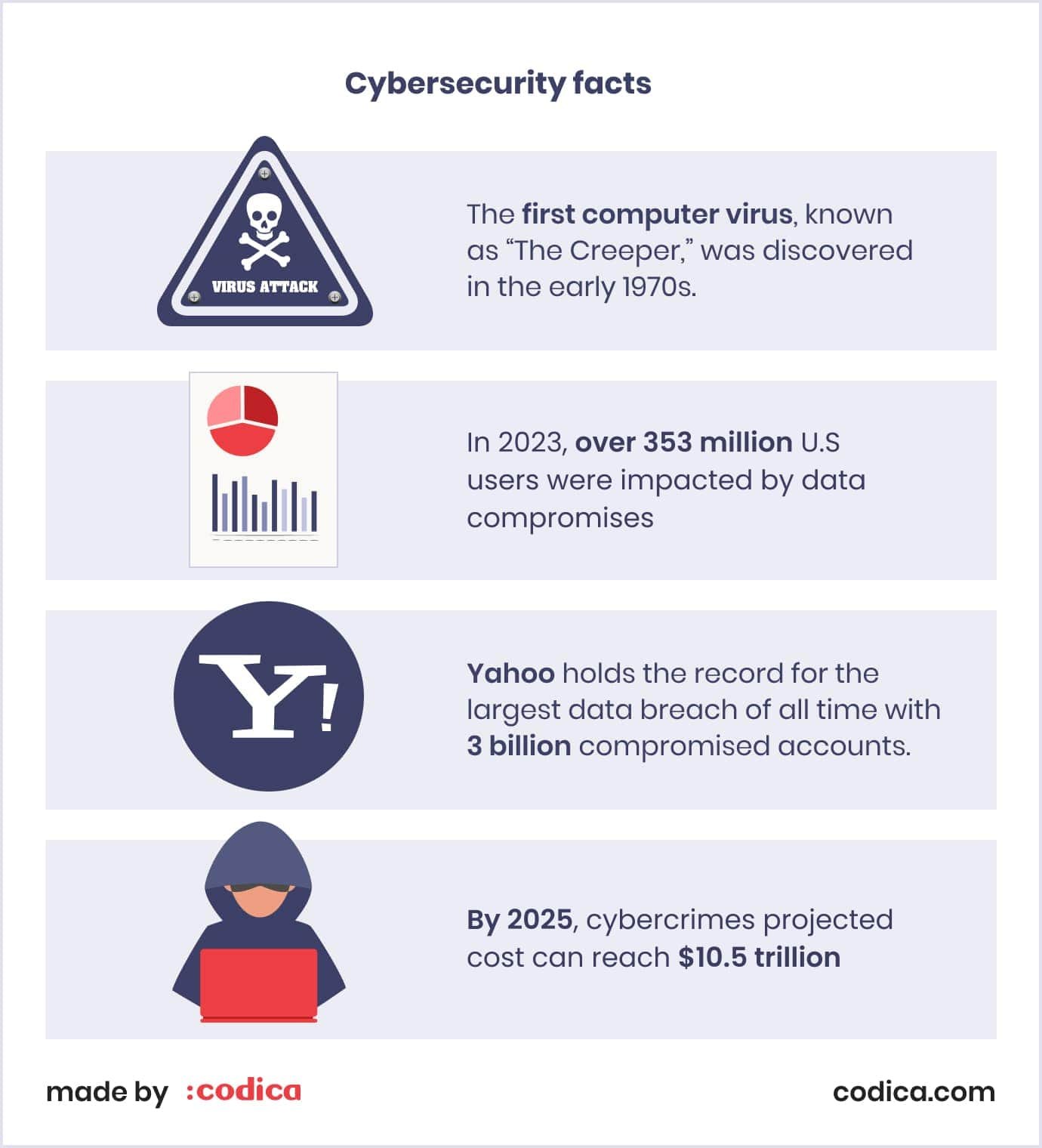
To sum up, SaaS applications security is crucial for several key reasons:
First of all, it is all about protecting sensitive data. SaaS applications often handle customer information, financial data, and intellectual property. Security breaches can lead to data theft and financial loss. Additionally, cybercrimes themselves can significantly damage your software. Things like malware, ransomware, and phishing attacks can put your users and the entire company at risk.
Secondly, maintaining customer trust is also crucial. Customers expect their data to be secure when using SaaS applications and rarely think twice before providing their personal details to the app. A security breach can erode trust and lead to customer churn, damaging your company's reputation and long-term viability.
Challenges in SaaS security
Although security is a must, it is also challenging to set up properly. To make it effective, you have to account for many aspects. Today’s industry poses many challenges, which are greatly connected to the business and economic side of things. Thus, some of them include:
Shortage of IT security professionals. The market for IT professionals, especially those working on cloud security, is tight, and companies compete fiercely to hire qualified specialists. Simply put, they work in a tight niche that can be difficult to apply to other fields.
Breaches and threats. As of today, data breaches are still the biggest issue for the entire cloud computing industry. For instance, studies show that almost 40% of businesses experience data breaches.
Overcrowded market. Due to ease of use and unpretentiousness, SaaS apps are extremely popular. In fact, they are used in all types of businesses, which, in turn, creates competition. Entering such a fierce market requires you to offer a unique product, showing users something they need but don’t have in other tools.
Cloud migration difficulties. According to another survey, 78% of companies experienced high demand and a lack of resources, which became a significant challenge in adopting cloud technology. Such issues can result in migration errors that jeopardize security.
Integration vulnerabilities. SaaS apps love to integrate with third-party software. It is a cool trick, allowing them to extend their functionality without overcomplicating the product. However, third-party software integrations can be a gateway for cybercriminals and pose a threat. Thus, you must thoroughly check the solutions you work with.
Read also: The Future of SaaS: Top SaaS App Development Trends for 2024
Layers of SaaS security
SaaS has many moving parts, and only protecting each of them ensures your solution is secure. Thus, let’s take a closer look at all of these parts and see why they’re so critical to protect.
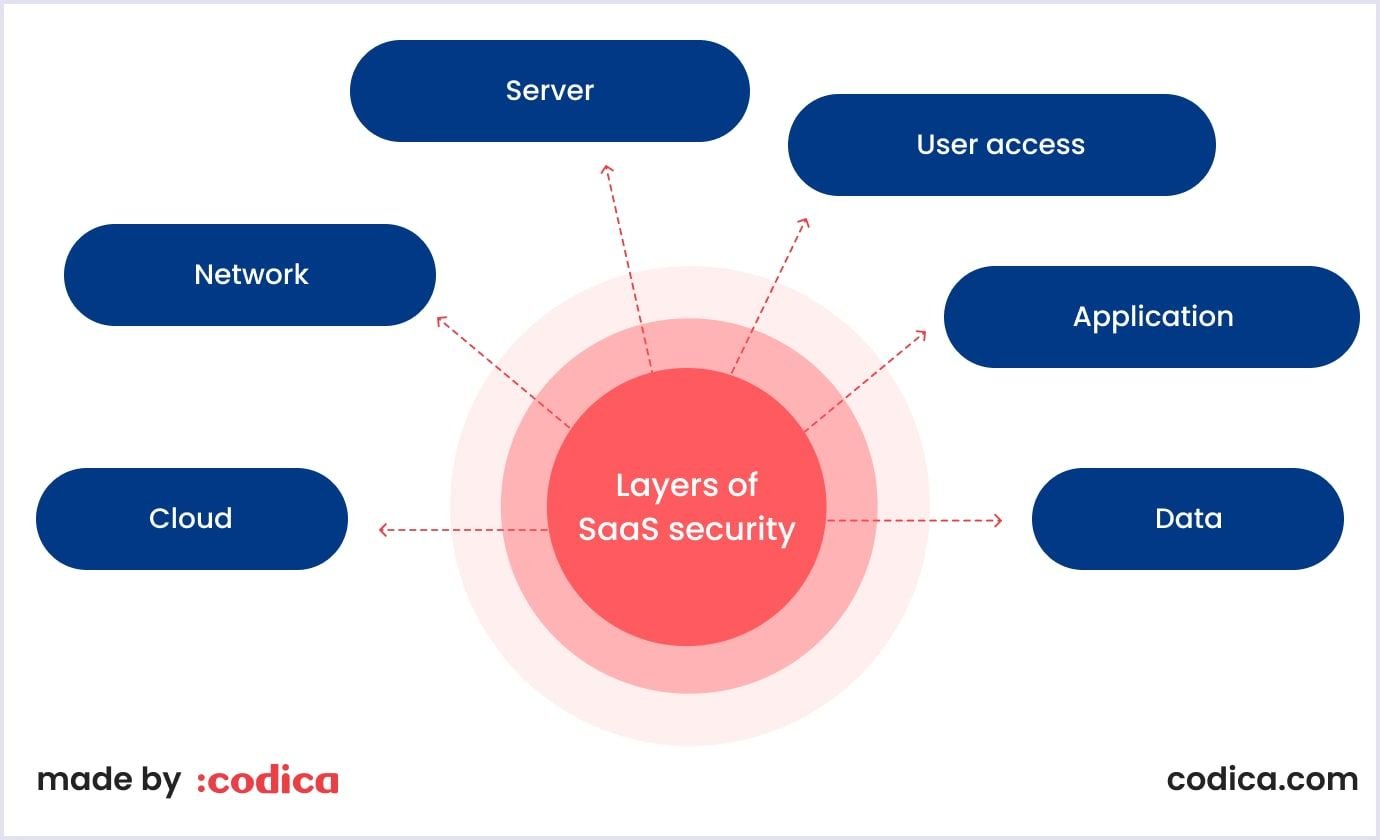
Cloud
SaaS services often rely on public cloud Infrastructure-as-a-Service (IaaS) providers. Securing this layer is critical, as compromised cloud credentials can render other security measures ineffective. Access should be restricted and multi-factor authentication enforced for all user accounts.
Read also: IaaS vs PaaS vs SaaS: Choosing the Best Cloud Computing Model
Network
Securing the network layer involves controlling traffic to ensure only authorized access. Major IaaS providers offer tools to limit exposure at this layer. Additional traffic filtering mechanisms may be employed depending on the setup.
Server
The server layer requires lockdown by limiting system components, hardening configurations, and ensuring regular patching. Configuration management systems aid in maintaining security, especially with continuous software updates.
User access
Perhaps the most vulnerable aspect of any system is user access. Thus, control over this access is crucial to prevent credential compromise and unauthorized access. SaaS security tools like Directory-as-a-Service help manage access efficiently, with multi-factor authentication and strong password policies enforced.
Application
The app itself can also be an entry point for risky situations. At the application layer, coding errors pose significant risks. Code reviews and penetration testing help identify vulnerabilities, including those in third-party libraries. Following guidelines like the OWASP Top 10 list is essential for securing applications.
Data
Working with data is another critical aspect of securing your product. Notably, protecting customer data involves encrypting it at rest and in transit. However, safeguarding encryption keys is equally important. The architecture of data storage, encryption, and decryption processes must be carefully planned to ensure maximum security, considering potential compromises.

SaaS app security issues
In 2023, cloud SaaS security issues constituted a threat of vulnerabilities and data breaches that cost companies $4.45 million dollars. In cybersecurity related to SaaS, there are common security threats and issues inherent to cloud computing. And most of the security risks are related to SaaS cloud security. It can be explained by the fact that the data is stored with a third-party provider and accessible over the Internet.
Let’s outline the most critical security issues for SaaS applications that security teams should be aware of.
Security misconfiguration. Dozens of reports and surveys state that it is the most common SaaS application security issue. Here, malicious activity is caused by an incorrect setup of computing assets. To ensure SaaS application security, it is essential to configure all the tools and upgrade them properly on time.
For example, manually detecting and remediating SaaS misconfiguration leaves organizations exposed. When businesses manually monitor and remediate their SaaS security settings, it is taxing on the DevOps services team and leaves the organization vulnerable.
Underinvestment in SaaS security tools and staff. Yearly, more and more companies increase their investments in business-critical SaaS apps. Yet, fewer organizations report increasing their investment in security tools and staff for cloud SaaS security. This change means an increasing burden on the existing security teams to monitor SaaS security risks.
Non-use of SSPM (SaaS Security Posture Management) tools. The use of SSPM tools (Cynet, Adaptive Shield) helps reduce the timeline to detect and remediate SaaS misconfigurations. Businesses utilizing an SSPM can detect and remediate their SaaS misconfigurations significantly quicker.
Identity theft. Data exchange, online payments, and other operations that are frequently used in SaaS products might pose risks of identity theft. To prevent this issue, you can use many security tools, such as firewalls, Lightweight Directory Access Protocol (LDAP), or encryption at rest and in transit.
Cross-site scripting (XSS). It is one of the most common data vulnerabilities, affecting nearly two-thirds of all applications. This type of attack means the injection of malicious code into pages viewed by end-users. The latest versions of Ruby on Rails or React can automatically prevent this SaaS web security threat.
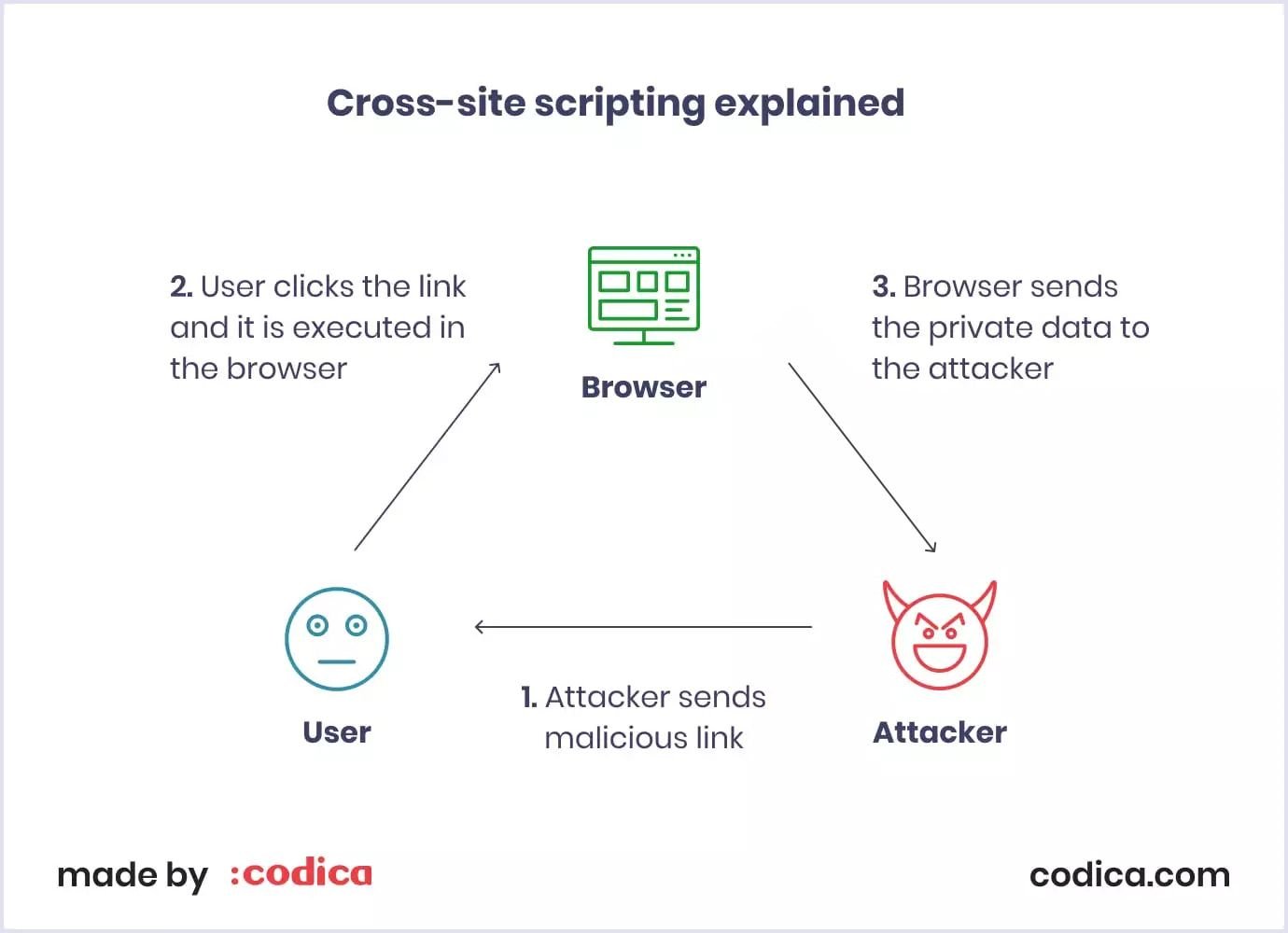
Source: Sqreen
All those SaaS application security issues can cause substantial data breaches and business losses. Mind that the costs of a data breach are higher for small businesses. Cloud security concerns have a massive impact on the cost of building a SaaS app.
SaaS security best practices
At Codica, we enhance the SaaS products we build with cutting-edge security measures. Some may seem obvious, while others are more complicated. Yet, in combination, they excel in making SaaS products truly secure.
Data encryption
This means that all interactions between the server and user happen over SSL connections and are encrypted. However, end-to-end encryption should also exist for data storage. Many providers have the option to encrypt the data by default, while some clients need to explicitly specify this. Clients can also have the option to encrypt specific fields, such as financial details, by using multi-domain SSL certificates.
Privacy is always a priority
Privacy and security statements are mandatory for compliance with regulatory protocols, yet their significance extends beyond mere compliance. Crafting a comprehensive statement for your product serves as an educational tool for both your team and your customers regarding the handling of sensitive data. Accordingly, we emphasize collaboration with our clients and legal teams to delineate the specific details that should be incorporated into your privacy policy.
Educate your customers
When bringing aboard new customers or implementing significant updates for existing ones, proactively communicate to inform them about the impact on their security. With many SaaS companies transitioning to cloud-based infrastructures, customers may not fully grasp the implications. Thus, we help you ensure customers understand how to safeguard their information to mitigate security concerns.

Back up user data in several locations
As we can see from previous examples, numerous businesses lack readiness for data breaches, underscoring the importance of effective customer data management. Maintaining backups in multiple locations safeguards against single system failures compromising security. While many cloud platforms offered by SaaS companies include this functionality, ensuring diligent backup practices is essential to prevent potentially catastrophic losses of customer data.
Consult your development partner
In the development of SaaS products, we engage our expert teams to advise our clients on security measures. Your development partner should offer valuable industry insights into securing your platform. Through our rigorous testing protocols, we guarantee the safety of your software, network, and infrastructure. Additionally, these third-party providers can assist in devising contingency plans in the event of a breach as you build your product.
Multi-factor authentication (MFA)
Multi-factor authentication is crucial for SaaS applications because it enhances security, protects against attacks, meets compliance requirements, provides user convenience, adapts to remote work, and is cost-effective. MFA adds layers of verification, reduces risks like phishing, helps meet regulations like the General Data Protection Regulation (GDPR), balances security with user experience, ensures secure access from any location, and offers strong security at a reasonable cost. Simply put, MFA is the new standard for logging into applications, and we make sure the solutions we develop account for this.
Use SaaS Security Posture Management (SSPM)
This type of management is used to enhance security in SaaS applications. SSPM ensures robust security measures are in place, providing continuous monitoring, compliance checks, and threat detection to safeguard against risks and maintain a strong security posture. It provides automated security tools for tracking security threats in SaaS applications. Misconfigurations, unused user accounts, excessive user rights, compliance hazards, and other cloud security problems are all detected by SSPM security.
Final words
We hope that this SaaS security checklist will help you build a fully-protected cloud application. Also, we would like to mention that it is crucial to keep in mind other aspects of building on-demand software. To get a profitable product, consider the best practices for building a SaaS startup.
We help our clients build robust and efficient cloud-based software that customers like to use. For this, we use the best practices to protect cloud applications from the loss of data threats. If you need any assistance in SaaS development services for your business, you can contact us right now. Our expert team is always ready to accept new challenges and help you with your SaaS project.
